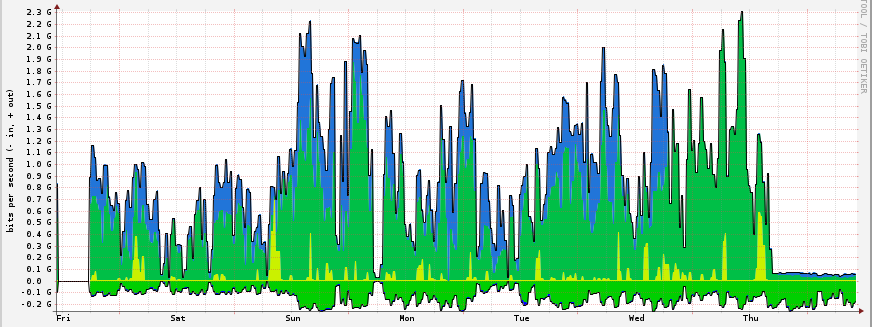
Paul Vlaar写了一封邮件,描述了RRL的一次DDoS防护效果。RRL发挥作用后将18万每秒的DNS查询量降低了80%,将2.3G每秒的攻击流量降低到70M。如下是邮件全文:
Hi all,
I just wanted to share this graph showing the effect of RRL during an
attack that we were seeing to a node of ours not doing RRL yet on that
particular nameserver.
We're still seeing spikes of up to 180k DNS queries per second, but due
to the RRL we're now at a rather steady rate of 80% query drop. Biggest
percentage I've seen so far. It does appear that for this particular
attack the source (probably spoofed) addresses are a relatively small
subset, so RRL is particularly effective at keeping traction here.
We went from ~2.3Gb/s to less than 70Mb/s on the outbound after we
turned on RRL. We're running BIND 9.8.3-vjs197.16-P4 here, and these are
the RRL config settings:
rate-limit {
responses-per-second 5;
errors-per-second 5;
window 15;
slip 5;
};
Obviously this is a huge improvement for everyone involved.
I hope this is of interest or inspiration to anyone. If anyone wants to
know more details, let me know.
Much thanks goes to the developers!
注意这个Paul不是RRL的作者Paul Vixie。DNS RRL目前以BIND的补丁形式存在,该项目一直想获取BIND的官方认可,但ISC似乎没这个意向。他们担心RRL在发挥作用的同时,也制造了新的漏洞被黑客利用。
Paul还附带了一张统计图来说明这个效果: